Many organizations continue to run business-critical systems on PowerBuilder. While these applications remain stable, their security architecture often reflects practices from earlier development periods.
Today, applications must meet stronger security expectations and, in many industries, formal compliance requirements. This creates a recurring question for teams maintaining existing systems:
How can a PowerBuilder application be secured without rewriting it?
A recently published PowerBuilder security guide proposes a structured roadmap that organizations can use to modernize security step by step. Rather than focusing only on code, the guide looks at the entire application lifecycle: development, deployment, data protection, access control, and audit readiness.
Common Security Risks in Existing PowerBuilder Systems
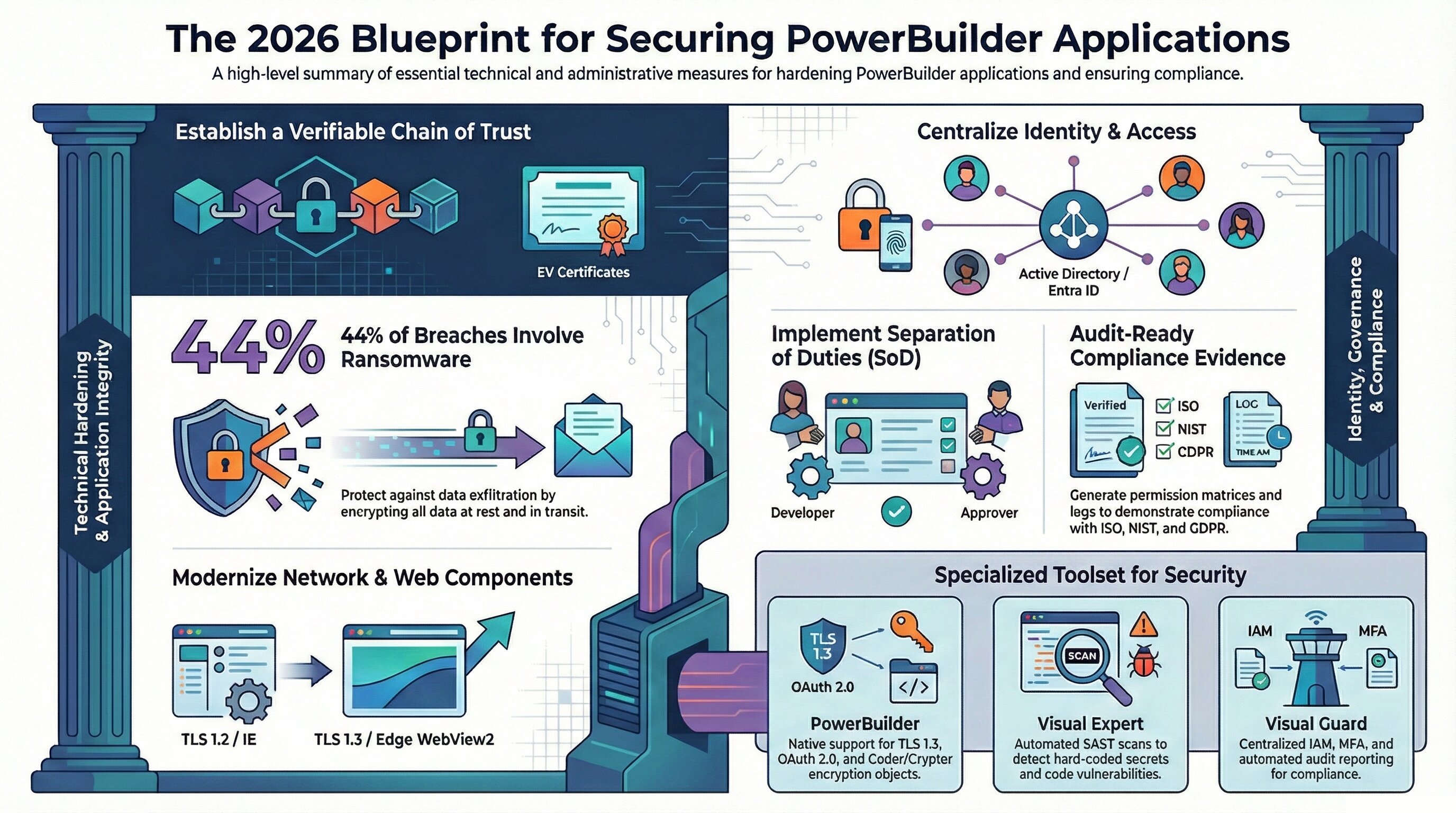
Security issues typically accumulate over years of maintenance and incremental changes. The guide highlights several recurring risk areas.
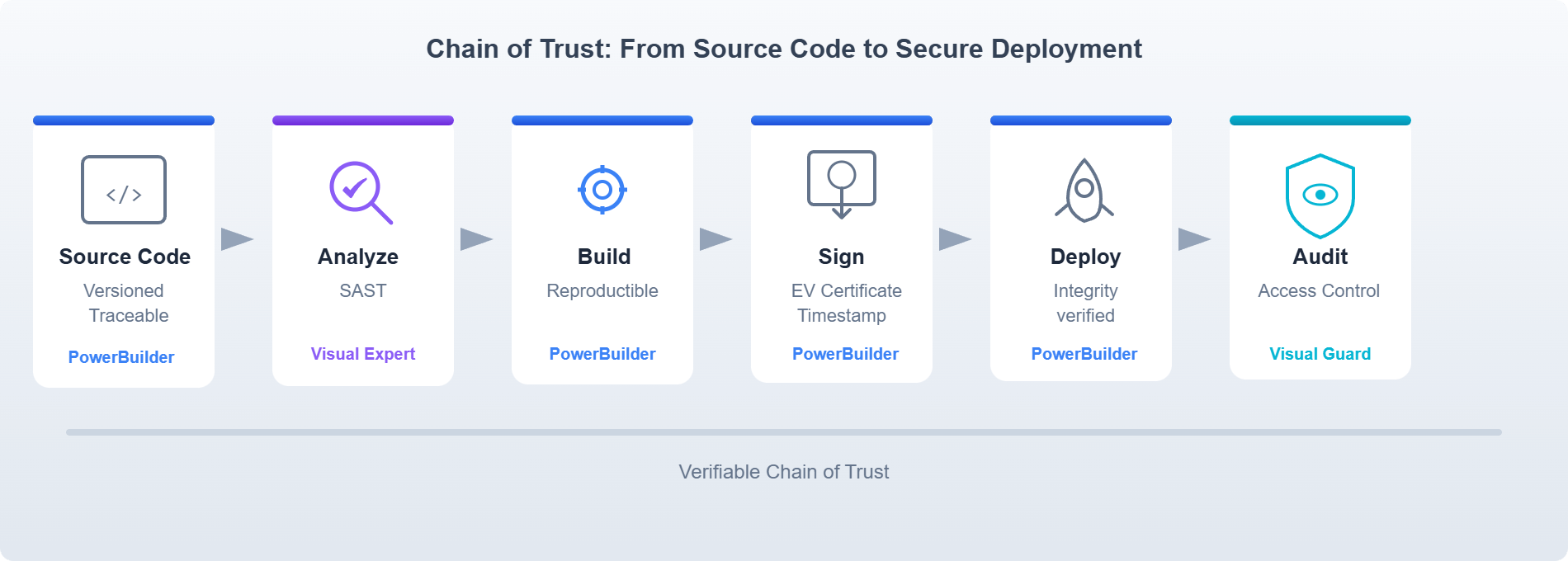
1. Software Supply Chain Risks
Executables and updates can be compromised during build or deployment. Incidents like SolarWinds and the 3CX breach showed how attackers can inject malicious code into legitimate update processes.
Without consistent and traceable build processes, signing, and artifact tracking, organizations may struggle to prove software integrity.
2. Exposure of Sensitive Data
Applications often transmit or store sensitive data without proper encryption, especially in legacy environments.
Healthcare and finance breaches frequently involve unencrypted storage or transmission.
3. Outdated Network Protocols
Older TLS versions or weak cryptographic configurations may still be in use. Modern infrastructure increasingly blocks such connections, creating both security and operational risks.
4. Weak Access Control Models
Applications using local user accounts or coarse permission models often cannot support:
- Separation of duties
- Role-based controls
- Audit requirements
- Centralized identity governance
5. Legacy Embedded Browser Components
Some applications still rely on outdated browser controls, exposing systems to vulnerabilities that are no longer patched.
Modern replacements reduce attack surface and ensure compatibility.
Practical Implementation Approach to Secure PowerBuilder Apps
The guide is designed as independent security improvement blocks that teams can adopt based on their risks, priorities, and available resources.
Common improvement areas include:
Core security improvements
Often achievable without major investment:
- Enable TLS encryption for database and network connections
- Identify and remove hard-coded credentials and secrets
- Sign executables and deployment packages
- Verify protocol versions actually used in production
Application modernization improvements
Typically handled as incremental improvement projects:
- Upgrade to recent PowerBuilder versions supporting modern protocols
- Replace legacy embedded browser components
- Integrate applications with centralized identity systems
- Implement structured audit logging and permission documentation
Structural and long-term improvements
Adopted when broader changes are planned:
- Automate vulnerability scanning of PowerBuilder code
- Implement role-based access control with periodic reviews
- Modernize API integrations using token-based authentication
- Move toward architectures that centralize security controls
Organizations can select only the blocks relevant to their context rather than attempting full modernization at once.
Security and Compliance Alignment for PowerBuilder Apps
In regulated industries, security improvements must also produce evidence usable during audits.
The controls described in the guide commonly support requirements found in standards such as ISO 27001, NIST SP 800-53, PCI DSS, HIPAA, SOX, and GDPR.
In practice, auditors typically expect evidence such as:
- Signed and traceable build artifacts
- Access control and permission documentation
- Static code analysis reports
- Audit log retention and monitoring records
- Encryption configuration details
- Network protocol validation results
Who Should Read This Guide?
The document is useful for:
- PowerBuilder developers maintaining legacy systems
- Security and infrastructure teams
- DevOps and release managers
- Audit and compliance teams
- IT leaders planning modernization
Final Note: A Practical Roadmap for 2026 and Beyond
PowerBuilder remains widely used in critical environments. Security challenges often stem not from the platform itself, but from accumulated technical debt and outdated practices.
If security is on your roadmap this year (and it should be), this is the definitive resource to set your PowerBuilder applications on the right track.